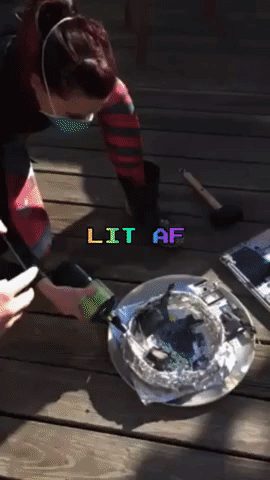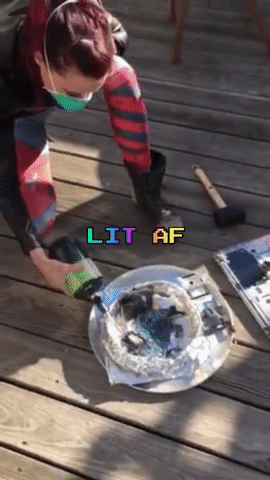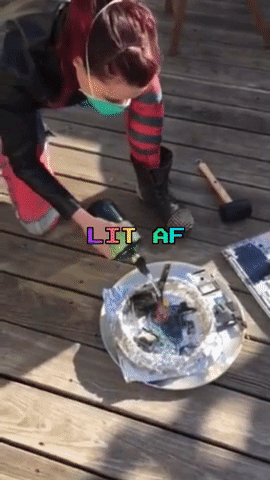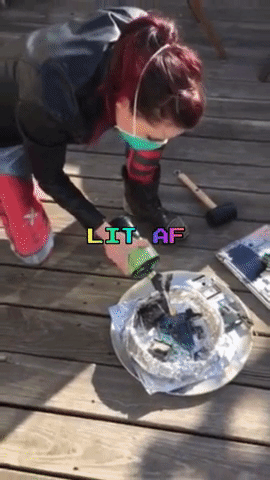Hidden in Plain Sight
Background
Powers of Tau is the latest Secure Multi-Party Computation protocol being used by the Zcash Foundation to generate the parameters needed to secure the Zcash cryptocurrency and its underlying technology in the future.
People from all over the world collectively generating these parameters is called the ceremony. As long as just one participant in the ceremony acts honestly and avoids having their private key compromised, the final parameters will be secure.
The below is a write-up of Amber Baldet and my own participation in that ceremony, with Robert Hackett of Fortune Magazine observing parts of the process.
Warning: The below contains fire.
The Theme of Our Participation
We live in New York City, one of the most surveilled and crowded places in the world. While others who have participated in the ceremony made explicit attempts to escape civilization and avoid surveillance, we thought it would be interesting to leverage the lack of privacy and the general inability to do things in secret in a large city in a way that nevertheless contributes to the creation of a technology that does give people back privacy.
As part of our participation, we wanted to sample the people of New York’s thoughts on personal privacy, and extract information from public places in a way that, even if somebody were following along and watching, our computation still had only a small chance of being compromised. In particular, we employed operational security tools such as only making cash payments, and making movements unpredictable. We also sought to prevent a possible adversary from:
- being able to deduce our plan
- being able to predict what items we will buy and where
- being able to continue following us, if they are
- discovering where we will perform the computation in time to deploy advanced attacks that don’t require physical access to our hardware
We did accept that doing this in NYC would make it nearly impossible to resist the active efforts of law enforcement. We did not attempt to thwart, nor did we notice, such an effort.
We dubbed this plan “Hidden in Plain Sight”.
Gathering Supplies
We begin on the morning of March 15th, 2018. Amber has bought:
- Several different kinds of dice
- Play-Doh to stuff into unused ports of hardware we will buy later
- A blow torch nozzle and two propane tanks to burn things
- A mallet to smash things
- Two large umbrellas even though it’s a beautiful sunny day
- Adhesive labels to make physical tampering of hardware and doors evident
We unpack the dice and pull up a list of electronics stores in Manhattan. Without clicking any of the options, which would reveal our choices to Google, we each roll dice to determine two stores to go to. Amber doesn’t tell me where she is going, and I don’t tell her. We turn off our phones and embark.
(We powered on our phones in flight mode a couple of times to take pictures.)
At each of the electronics stores, we’re looking for:
- A portable video camera similar to a GoPro
- A MicroSD memory card for the camera
- An SD card reader
We roll dice to determine both which of the available camera and SD card options to pick from, and then again to determine which of the items on the shelf to buy. The store employees don’t seem to care about our behavior–just another day in New York, I guess.
Meanwhile, Amber meets up with Robert Hackett and goes to a print shop where she selects via dice roll a workstation on which to type up a note containing the note “Thank you for participating! You can learn more about the project here:” and a QR code linking to the Powers of Tau page.
We rendezvous again in Union Square. Over lunch at a randomly selected location, we unpack and charge the cameras, making sure that they are within sight at all times.
Gathering Entropy
Good toxic waste for use in a Powers of Tau computation contains a high amount of randomness, or entropy. We can’t rely on the entropy collectors in computers–what if they’re all broken? So the first task at hand is collecting randomness that an adversary would have to spend a very large amount of money to replicate.
Amber prepares a sign intended to pique people’s curiosity.
I turn on the first camera, and we both pop open our umbrellas. The umbrellas are intended to obscure the view of any eyes in the sky.
I hit record, and Amber starts approaching strangers.
A couple from Canada is curious why we have umbrellas out when it’s sunny, and we sit down next to them.
During the conversation, Amber asks, “How do you feel about the statement ‘If you haven’t done anything wrong, you’ve got nothing to hide’?”.
The man replies, “I would say that that’s accurate.”
“That’s accurate?”, Amber asks, seeking confirmation.
“Absolutely,” he says.
We go over to two men sitting on a metal fence surrounding the shrubbery. After a bit of small talk, Amber again poses the question, “What do you think about the statement ‘If you’re not doing anything wrong, you’ve got nothing to hide’?”
The man shakes his head before pronouncing, “That’s complete, complete bullshit. The government will always spy on what you’re doing if they want to. And what you’re doing that’s not wrong today may be wrong tomorrow. What you think isn’t wrong they might think is wrong.”
Our last conversation in Union Square is with a guy who’s had just about enough of his friend talking about cryptocurrencies. “My friend talks about so many different ones. I can’t even remember any of them.”
“Let me just put down my spliff here,” he says as he realizes we’re recording.
Amber asks if he’s heard that Bitcoin is anonymous and private.
“Yes, I have,” he says.
“Do you think that’s true?”, she asks.
“No, I don’t,” he replies.
We get on the 6 train toward Grand Central. Moving quickly through the underground tunnels of the city in a metal tube, I again start recording. Even though I’m only recording people’s feet, a local New Yorker is not impressed. “Get a picture for your ass!”, she yells.
Walking through the tunnels of Grand Central, we encounter a group of Hare Krishna monks playing music. I hit record and we stop to talk to one of them.
“Have you ever heard of Bitcoin?”, Amber asks.
“Yes”, he says, exasperatedly, seemingly unimpressed by the cryptocurrency trend.
A little later, Amber asks him, “What’s the greatest secret?”
He replies, “Everyone is dying around you, and yet everyone thinks it’s not gonna happen to them. How to figure out the solutions to birth, death, disease and belief, these are the real questions, not how many Bitcoins do I have in my imaginary whatever account.”
I thank him for his time. As we turn toward the S train to Times Square, Amber asks offhand if he knows the current price of Bitcoin. “I dunno,” he says, “about ten thousand?”
As we get out of the subway station at Times Square, I pull out the other camera and hit record, capturing little bits of a heightened police presence, thousands of visitors to the city, and, of course, Elmo. We make an explicit decision not to approach Elmo, as getting in a fistfight may compromise our mission.
On the red stairs in the center of Times Square, we again open our umbrellas and have another few conversations.
Preparing for the Computation
Now that we’ve collected a sufficient amount of information that would be hard to replicate, we seal up the cameras and put them away. Next up is obtaining the hardware that will be used to perform the computation.
We set out towards a random electronics store.
Once at the store, we again roll dice to determine a laptop to buy, and which of the boxes to choose. We end up with a Celeron-powered Lenovo laptop with 2GB RAM and 32GB disk space.
(We tried to find a laptop with an ARM processor, a hardware configuration that hasn’t been used very much in the ceremony, but the store had none.)
The sales representative asks us what we’re going to use the laptop for.
“Doing one thing and then destroying it,” I reply.
“Oh, ok. Would you like to add extended warranty?” he continues.
I politely decline.
Performing the Computation
We select a hotel by dice roll and go there to get a room for one night. That we’re three people with several umbrellas, a bunch of unopened electronics, and no luggage doesn’t faze the hotel staff.
“Can we get a room facing toward the back?” I ask.
“Yes, this is in the back” the attendant replies.
For once I am excited to hear this.
To complete check-in I’m forced to provide identification and a credit card, compromising our position without necessarily revealing which room we’re in. (Being a real spy with a fake ID would’ve helped here.)
We get to the room and turn on the white noise generator conveniently installed in the window. We unbox the laptop and immediately install:
- Ubuntu 16.04.4 - SHA256:
3380883b70108793ae589a249cccec88c9ac3106981f995962469744c3cbd46d - Go 1.10 - SHA256:
b5a64335f1490277b585832d1f6c7f8c6c11206cba5cd3f771dcb87b98ad1a33 - The zip file of Filippo Valsorda’s alternative Go implementation of the Powers of Tau algorithm at commit
e2af113817477d26e6155f1aae478d3cb58d62c5- SHA256:fc473838d4dcc6256db6d90b904f354f1ef85dd6615cca704e13cfdd544316fe
During the OS installation the disk is encrypted using LUKS/dm-crypt using a very long, random password that is written down and later destroyed.
We make sure the laptop’s radio transmitters, like Wi-Fi and Bluetooth, are disabled. Then we copy the video files from both cameras to the hard drive and split them into one-megabyte chunks. We then randomly select a sequence of these chunks using /dev/urandom, and feed that sequence of video files into a hash function, producing some of our toxic waste.
We modify the taucompute source code to use a different cryptographically secure random number generator than the /dev/urandom one, seed it with the toxic waste, some random data from the system, a series of dice rolls, and some confidential inputs from both Amber and myself, and start the computation.
(These rolls were not used.)
The laptop is pretty poor, and the computation ends up taking much longer than expected. (We had been hoping to run it a number of times to increase the odds that a compromise would be revealed.) Robert and Amber both head out, and I wait for the computation to complete, wondering a couple of times if somebody is blasting the room with radiation to try to extract the toxic waste.
(This kind of attack as well as electromagnetic analysis isn’t something we explicitly tried to guard against other than by making our location hard to predict.)
At around 2 AM the computation completes. I copy from the laptop the response file along with its BLAKE2b checksum:
The BLAKE2b hash of `./response` is:
3eee603c e0feaaf9 47655238 7636462b
56bcba97 2b0e4b79 513b6ffc 8ba323d1
8574c79c ab756800 cae43440 6fa99eca
8445da3d e20b9af7 665325ff 89993df8After disconnecting power from the laptop (thus requiring re-entry of the encryption password), I seal up the laptop and memory cards used, and head home. Once at home, I seal up the doors and hide the hardware deep in my closet, in a place that could not be reached without waking me up.
(At the time of writing, it does not feel like I was drugged.)
Destroying the Secrets
The next day, Amber, Robert and myself meet up again, this time on Amber’s rooftop. Armed with propane and a blow torch nozzle, a mallet, and a fire extinguisher (just in case), we incinerate and smash the memory cards and laptop.
After a good deal of catharsis and minimal inhalation of plastic fumes, we are done: We did our part of the Powers of Tau ceremony, and were reminded to not take life for granted along the way.
Hopefully nobody was able to extract our toxic waste before we destroyed it!
Many thanks to Jason Davies for coordinating our participation, and to the whole Zcash team for creating a solid technology that genuinely benefits humanity.